2025’s Top Phishing Trends And What They Mean For Your Security...
2025 saw a huge amount of attacker innovation when it comes to phishing attacks, as attackers continue to double down on identity-based techniques. The continual evolution of phishing means it remains one of the most effective methods available to attackers today — in fact, it’s arguably more effective than ever.
Let’s take a closer look at the key trends that defined phishing attacks in 2025, and what these changes mean for security teams heading into 2026.
We’ve been talking about the rise of non-email phishing for some time now, but 2025 was the year phishing truly went omni-channel.
Although most of the industry’s data on phishing still comes from email security vendors and tools, the picture is starting to change. Roughly 1 in 3 phishing attacks detected by Push Security were delivered outside of email.
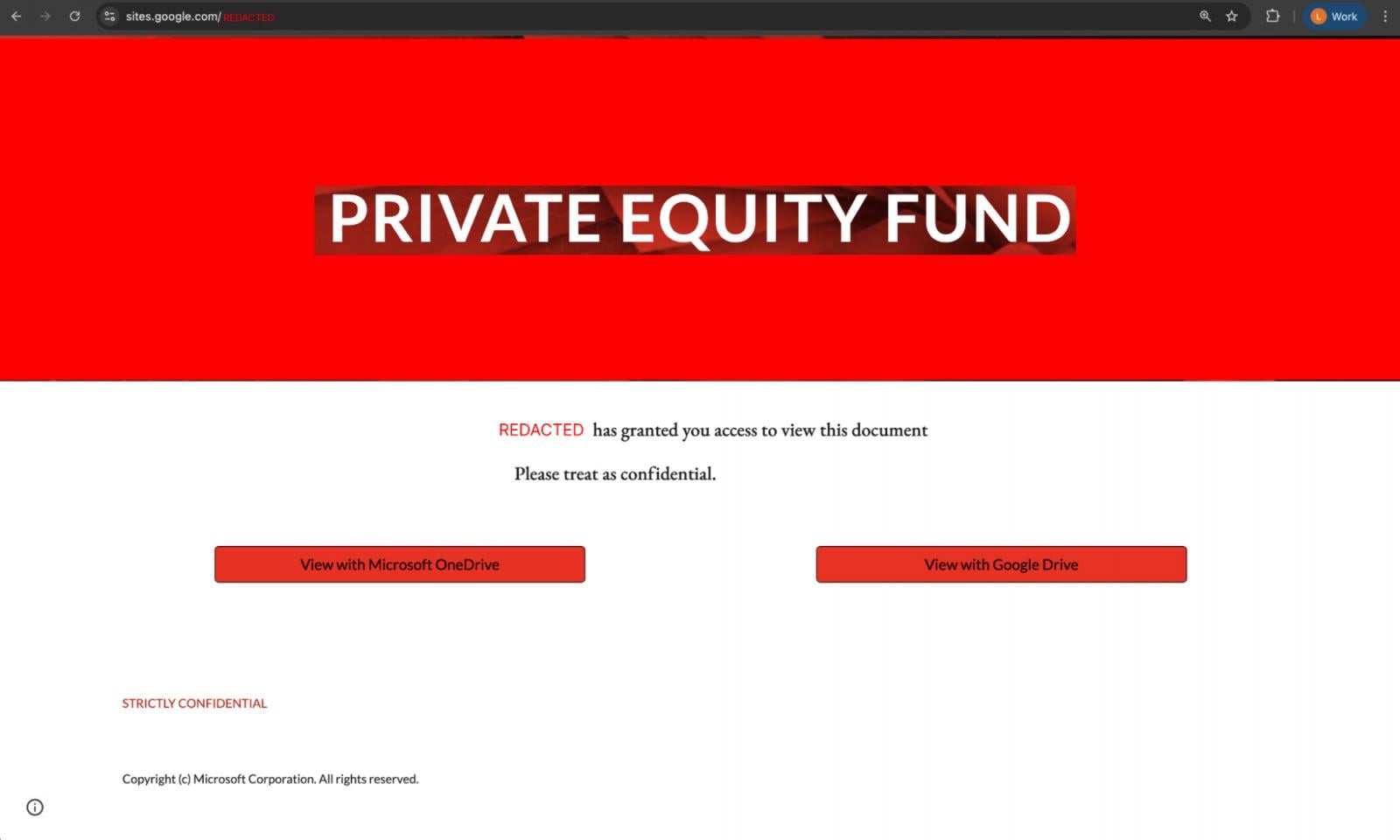
There are many examples of phishing campaigns operated outside of email, with LinkedIn DMs and Google Search being the top channels we identified. Notable campaigns include:
A targeted campaign against tech company Exec’s delivered via compromised accounts on LinkedIn from other employees of the same organization, framed as an investment opportunity.
A campaign posing as a South American investment fund offering the opportunity to join the fund.
Several malvertising campaigns capturing users searching for key search terms such as “Google Ads”, “TradingView” and “Onfido”.
Phishing via non-email channels has a number of advantages. With email being the best protected phishing vector, it sidesteps these controls entirely. There’s no need to build up your sender reputation, find ways to trick content analysis engines, or hope your message doesn’t end up in the spam folder.
In comparison, non-email vectors have practically no screening, your security team has no visibility, and users are less likely to anticipate possible phishing.
Source: BleepingComputer



