Complete Guide to Consentfix Debrief: Insights From The New Oauth Phishing Attack
In December, the Push Security research team discovered and blocked a brand new attack technique that we coined ConsentFix. This technique merged ClickFix-style social engineering with OAuth consent phishing to hijack Microsoft accounts.
We saw this attack running across a large network of compromised websites that attackers were injecting the malicious payload into, forming a large-scale campaign that was detected across multiple customer estates.
ConsentFix got a pretty awesome response from the community in a very short space of time.
Within days, John Hammond shared a new and improved version of the technique that he’d spun up in his own lab, while security researchers from Microsoft, Glueck Kanja, and other individual contributors all shared analysis and recommendations.
In this blog, we’re sharing some new insights on the campaign, pulling together some of the top recommendations and resources shared across the community, and looking forward to what the future holds for this novel technique as it quickly enters the mainstream.
First though, let’s quickly recap what ConsentFix is and how it works.
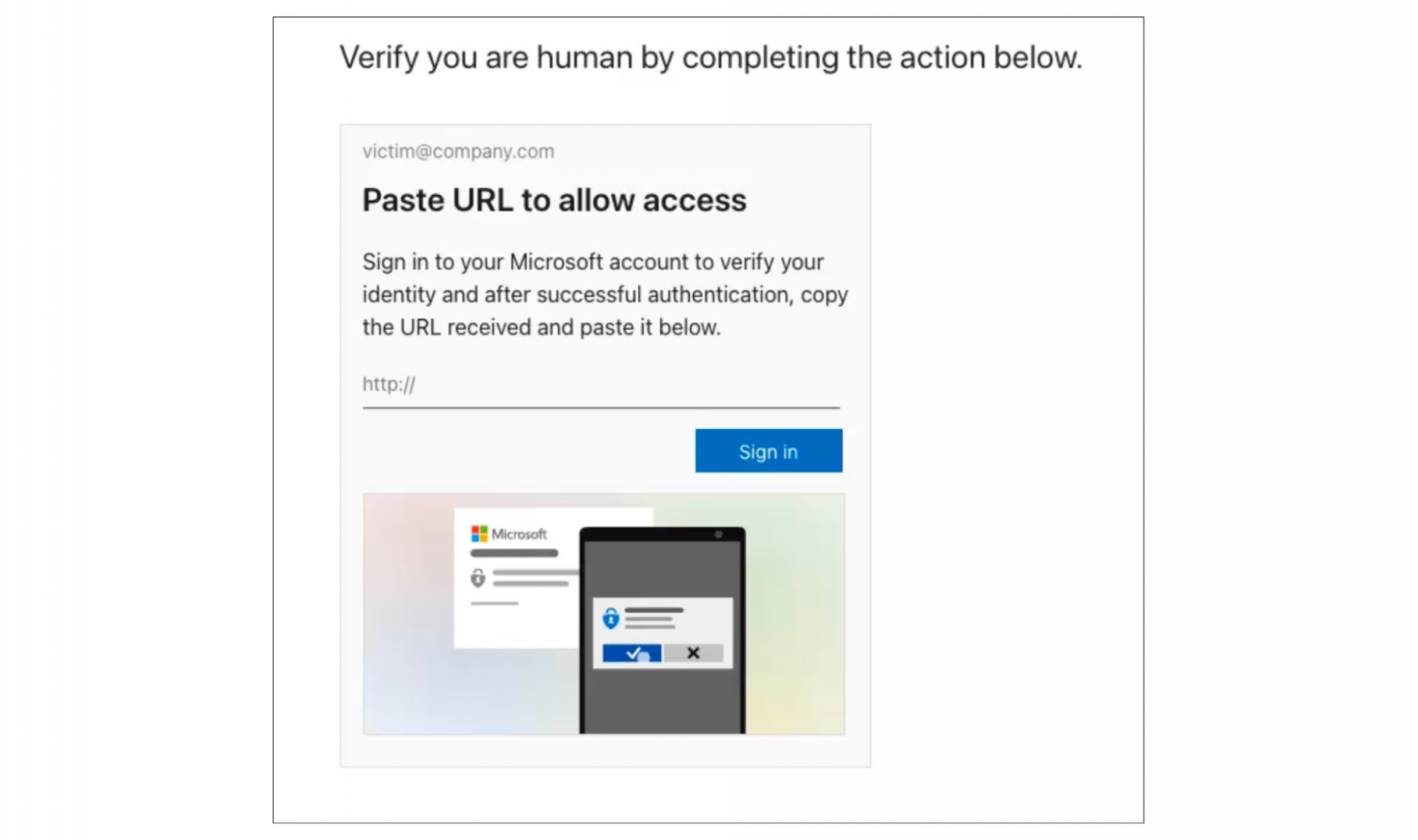
ConsentFix is an attack technique that prompts the victim to share an OAuth authorization code with an attacker via a phishing page. The attacker then enters this code into a target application on their own device in order to complete the authorization handshake and take over the account.
By hijacking OAuth, attackers can effectively bypass identity-layer controls like passwords and MFA — even phishing resistant authentication methods like passkeys have no impact on this attack, because it sidesteps the authentication process altogether.
OAuth abuse attacks are not new. Techniques like consent phishing and device code phishing have been around for some time.
However, these mainly focus on connecting your primary workspace account (e.g. Microsoft, Google, etc.) to a fraudulent, attacker-controlled application. But this is becoming increasingly difficult in core enterprise cloud environments like Azure due to stricter default configs. That said, device code phishing still featured prominently in the recent high-profile Salesforce attacks in 2025.
Source: BleepingComputer



