Hackers Exploit Wordpress Plugin Post Smtp To Hijack Admin Accounts
Threat actors are actively exploiting a critical vulnerability in the Post SMTP plugin installed on more than 400,000 WordPress sites, to take complete control by hijacking administrator accounts.
Post SMTP is a popular email delivery solution marketed as a feature-rich and more reliable replacement of the default ‘wp_mail()’ function.
On October 11, WordPress security firm Wordfence received a report from researcher ‘netranger’ about an email log disclosure issue that could be leveraged for account takeover attacks.
The issue, tracked as CVE-2025-11833, received a critical-severity score of 9.8 and impacts all versions of Post SMTP from 3.6.0 and older.
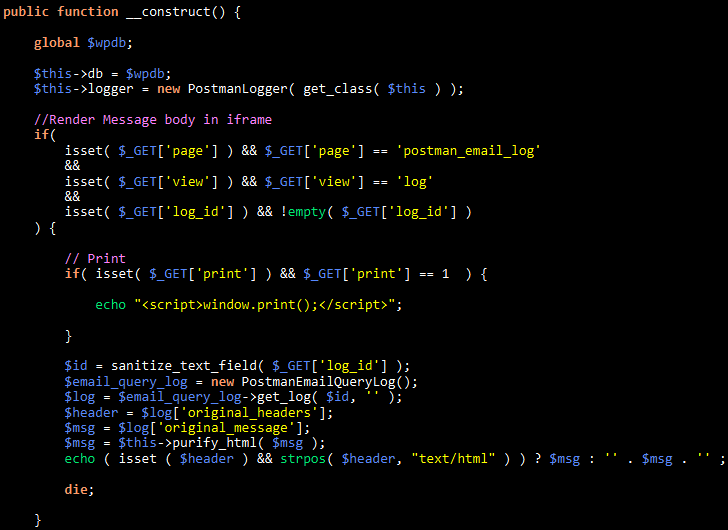
The vulnerability stems from the lack of authorization checks in the ‘_construct’ function of the plugin’s ‘PostmanEmailLogs’ flow.
That constructor directly renders logged email content when it is requested without performing capability checks, allowing unauthenticated attackers to read arbitrary logged emails.
The exposure includes password reset messages with links that allow changing an administrator’s password without the need of a legitimate account holder, potentially leading to account takeover and full site compromise.
Wordfence validated the researcher’s exploit on October 15 and fully disclosed the issue to the vendor, Saad Iqbal, on the same day.
A patch arrived on October 29, with Post SMTP version 3.6.1. Based on WordPress.org data, roughly half of the plugin’s users have downloaded it since the release of the patch, leaving at least 210,000 sites vulnerable to admin takeover attacks.
According to Wordfence, hackers started exploiting CVE-2025-11833 on November 1. Since then, the security firm has blocked over 4,500 exploit attempts on its customers.



