Update: Hidden Telegram Proxy Links Can Reveal Your Ip Address In One Click
A single click on what may appear to be a Telegram username or harmless link is all it takes to expose your real IP address to attackers due to how proxy links are handled.
Telegram tells BleepingComputer it will now add warnings to proxy links after researchers demonstrated that specially crafted links could be used to reveal a Telegram user's real IP address without any further confirmation.
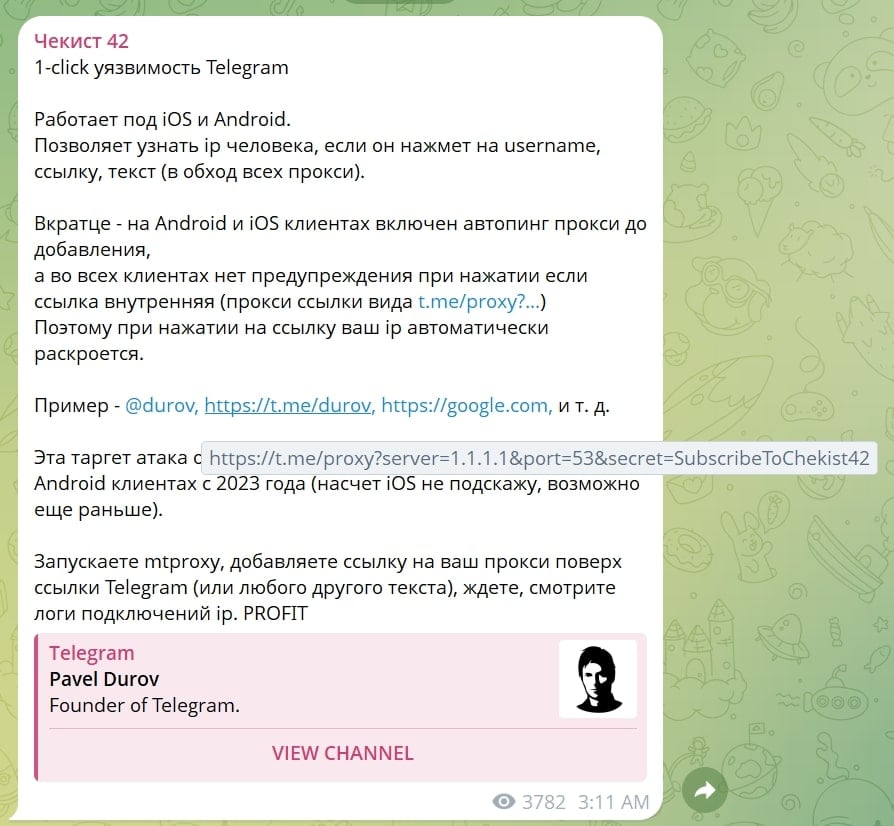
Security researchers have demonstrated this week that Telegram clients on both Android and iOS automatically attempt to connect to a proxy when a user taps a specially crafted internal link.
These links can be disguised as ordinary usernames, for example, appearing as @durov in a Telegram message, but actually lead to a Telegram proxy link.
Telegram proxy links (t.me/proxy?...) are special URLs used to quickly configure MTProto proxies in Telegram clients. They allow users to add a proxy by clicking a link instead of manually entering server details:
https://t.me/proxy?server=[proxy IP address/hostname]&port=[proxy_port]&secret=[MTProto_secret]
When opened in Telegram, the app reads the proxy parameters (including the server, port, and secret), and prompts the user to add the proxy to their settings.
These links are widely shared to help users bypass network blocks or internet censorship and to conceal their real location, particularly in restrictive environments, making the feature valuable to activists, journalists, and others seeking anonymity.
On Telegram's Android and iOS clients, opening a proxy link also triggers an automatic test connection, causing the app to initiate a direct network request from the user's device to the specified server before the proxy is added.
Attackers can abuse this behavior by setting up their own MTProto proxies and distributing links that are visually disguised as harmless usernames or website URLs but actually point to proxy configuration endpoints.
Source: BleepingComputer



